Institutions rarely choose a credential standard deliberately.
They choose what works today. A system that issues quickly. A credential that looks professional. A setup that fits neatly into the tools they already use. Sometimes that means a built-in LMS feature. Sometimes a vendor-managed credential platform. Sometimes a homegrown solution stitched together over time.
Only later does the harder question appear.
What happens to this credential once it leaves our system?
That question has become unavoidable today. Digital credentials no longer sit quietly inside institutional platforms. They travel. They are shared, verified, questioned, and revisited years after issuance, often by people who have no relationship with the issuing institution.
This is where the difference between Open Badges standards and proprietary credential systems stops being technical and starts being strategic.
This article is not about visual formats or badge aesthetics. If you’re evaluating digital credentials from a standards or governance perspective, this page is meant to act as a reference point. You can explore how verification works, how platforms differ, and where institutions typically face long-term risk as credentials scale.
It is about risk, durability, and what you're probably committing to when you decide how your credentials are structured.
Why Credential Standards Now Shape Institutional Credibility
Digital credentials used to be simple artifacts.
They were issued, downloaded, and stored locally. Verification was rare and often informal. Standards mattered mostly to technologists, not to institutional leaders making policy or governance decisions.
That context no longer exists.
Today, credentials are reviewed by employers who have never heard of the issuing institution. They are checked by automated systems that expect machine-readable proof. They are stored in wallets, linked on profiles, and evaluated far outside the issuer’s control.
In this environment, the standard behind a credential quietly determines whether it remains trustworthy over time.
By 2026, credential standards influence institutional reputation even when institutions never talk about them explicitly. When verification is smooth, the institution looks credible. When it is fragile, the institution absorbs the doubt.
What Open Badges Standards Actually Represent
Before going further, it helps to clarify what “Open Badges” means today.
Open Badges is not a visual format. It is an open credential standard.
With the most widely used implementation being Open Badges 2.0, the standard defines how a credential carries issuer identity, criteria, evidence, metadata, and verification data in a way that is independent of any single platform or vendor.
This is also why Open Badges are frequently discussed alongside global standards in digital credentials, rather than as a standalone format. Standards only matter when they are recognized beyond the issuing institution. Their value shows up when credentials move across borders, systems, and verification contexts without losing meaning.
In practical terms, this means the credential can still be verified even if it moves away from the system that originally issued it. The verification logic travels with the credential itself.
That openness is the defining feature.
It is not about ideology, decentralization rhetoric, or technology trends. It is about survivability. A credential designed on an open standard assumes that systems change, platforms evolve, and institutions restructure over time.
How Proprietary Credential Systems Are Typically Structured
Proprietary credential systems are built around control and tight integration.
Credentials are issued, stored, and verified within a single platform, a vendor-controlled environment, or a closed credential ecosystem. Verification depends on that system remaining available, unchanged, and authoritative.
From the inside, this feels efficient. Everything is managed in one place. Design is consistent. Workflows are streamlined. Ownership feels clear.
The credential works as long as the system works.
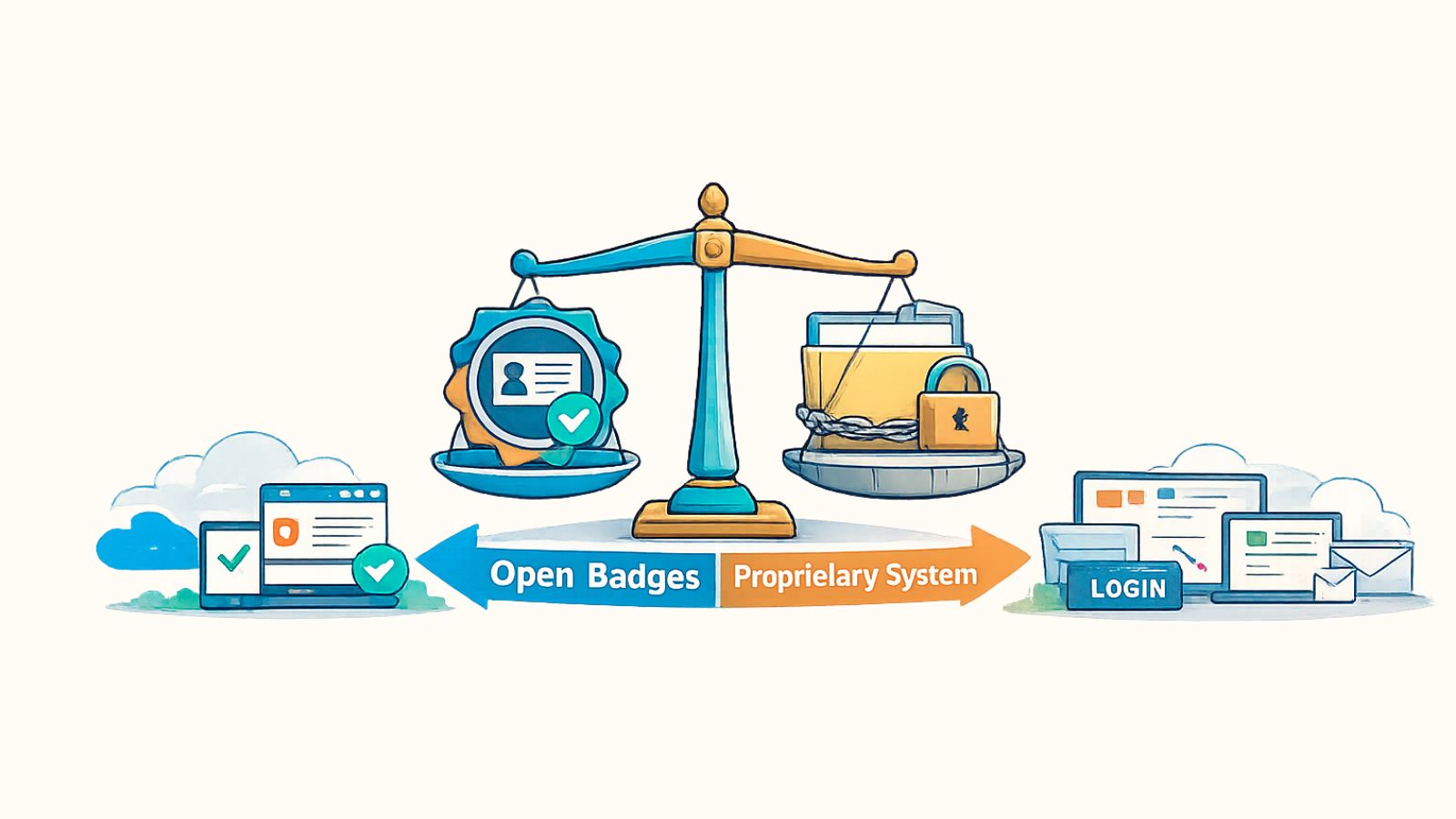 That dependency is the trade-off, and it often goes unnoticed until something shifts.
That dependency is the trade-off, and it often goes unnoticed until something shifts.
when digital credential portability becomes non-negotiable
Portability is rarely prioritized early.
Institutions assume credentials will be accessed within familiar environments. They expect learners to return to the same portal. They assume verification will happen within known networks or trusted platforms.
Only later do credentials start appearing in places the institution does not control.
A learner shares a credential on a professional profile. An employer clicks to verify. A third-party system attempts to parse it automatically, without human explanation or context.
Open Badges standards are designed for this reality. The verification data travels with the credential itself, allowing it to function independently of the issuing platform.
Platform-dependent credentials require verifiers to trust that the issuing system will always remain available, accessible, and stable.
That assumption usually holds, until it doesn’t.
How Verification Workflows Expose Long-Term Risk
Credential verification is where standards stop being abstract.
With Open Badges standards, verification does not require logging into a specific system or navigating a proprietary interface. The credential itself contains what is needed to confirm authenticity, issuer identity, criteria, and status.
With proprietary credential platforms, verification is centralized. If the issuing system changes its infrastructure, alters verification endpoints, or sunsets features, verification is affected downstream.
Neither approach is inherently wrong. But the risk profile is fundamentally different.
By 2026, verification is increasingly automated. Systems check credentials without human follow-up. Open standards align naturally with this future. Closed systems require continuous maintenance to keep pace. This distinction becomes clearer when you look closely at what makes a digital badge verifiable in the first place. Verification is not just about confirming issuance, but about whether authenticity, issuer identity, and criteria can still be proven outside the original system.
Why credential verification matters to employers, more than they admit
Employers rarely ask which standard a credential follows.
What they care about is friction.
If a credential verifies instantly and consistently, it is trusted. If it requires explanation, manual confirmation, or platform-specific steps, it becomes a hurdle in an already compressed decision process.
Open Badges standards reduce friction by design. They allow credentials to stand on their own, without requiring additional context.
Vendor-controlled credential formats can still work well, but usually only within defined ecosystems where expectations are shared.
Trust, in this context, is operational rather than philosophical.
Where proprietary and closed credential systems still make sense
This is not an argument against proprietary systems in all cases.
Closed credential systems can be effective when credentials are meant to stay within a controlled environment. Internal training programs, platform-specific achievements, or short-lived credentials may benefit from tight integration and design control.
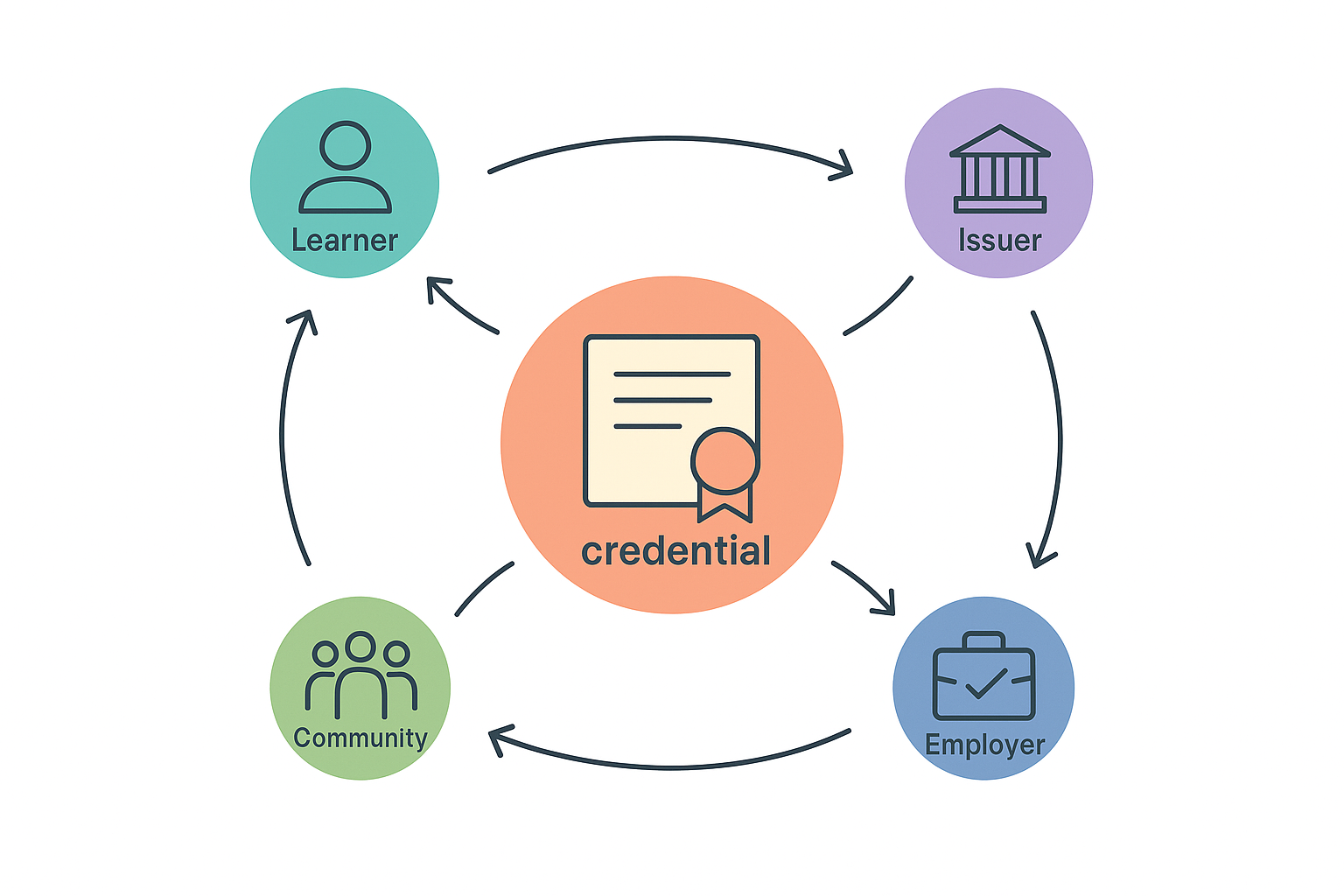
Problems arise when proprietary credentials are treated as portable proof rather than contextual signals.
That mismatch creates long-term risk, not because the credential is invalid, but because it was never designed to travel.
Credential Lock-In and Long-Term Risk
Lock-in is rarely obvious at issuance.
It becomes visible years later, when institutions attempt to migrate systems, change vendors, or respond to new compliance requirements. Many of these constraints trace back to earlier choices between LMS issued badges vs digital credentialing platforms, even if they did not feel significant at the time. What initially looked like a tooling decision often becomes a governance problem years later. Lock-in is rarely intentional, but it is almost always cumulative.
If credential data cannot be exported cleanly, re-verified independently, or retained outside the original platform, institutions lose leverage. Decisions become constrained by past technical choices.
Open Badges standards reduce this risk because the standard exists outside any single vendor.
Proprietary credential systems place long-term trust in the issuing platform’s stability, roadmap, and priorities.
Interoperability Expectations in Modern Credential Ecosystems
Credentials are no longer evaluated only by humans.
They are parsed by learning systems, hiring platforms, credential wallets, and verification services that expect structured, interoperable data.
Open credential standards assume a multi-system future.
Proprietary platforms can achieve interoperability, but often through custom integrations that require ongoing maintenance and coordination.
The difference may seem subtle early on. Over time, it compounds.
How learners experience credential standards years later
Learners rarely think about standards at the moment of issuance.
They think about access later.
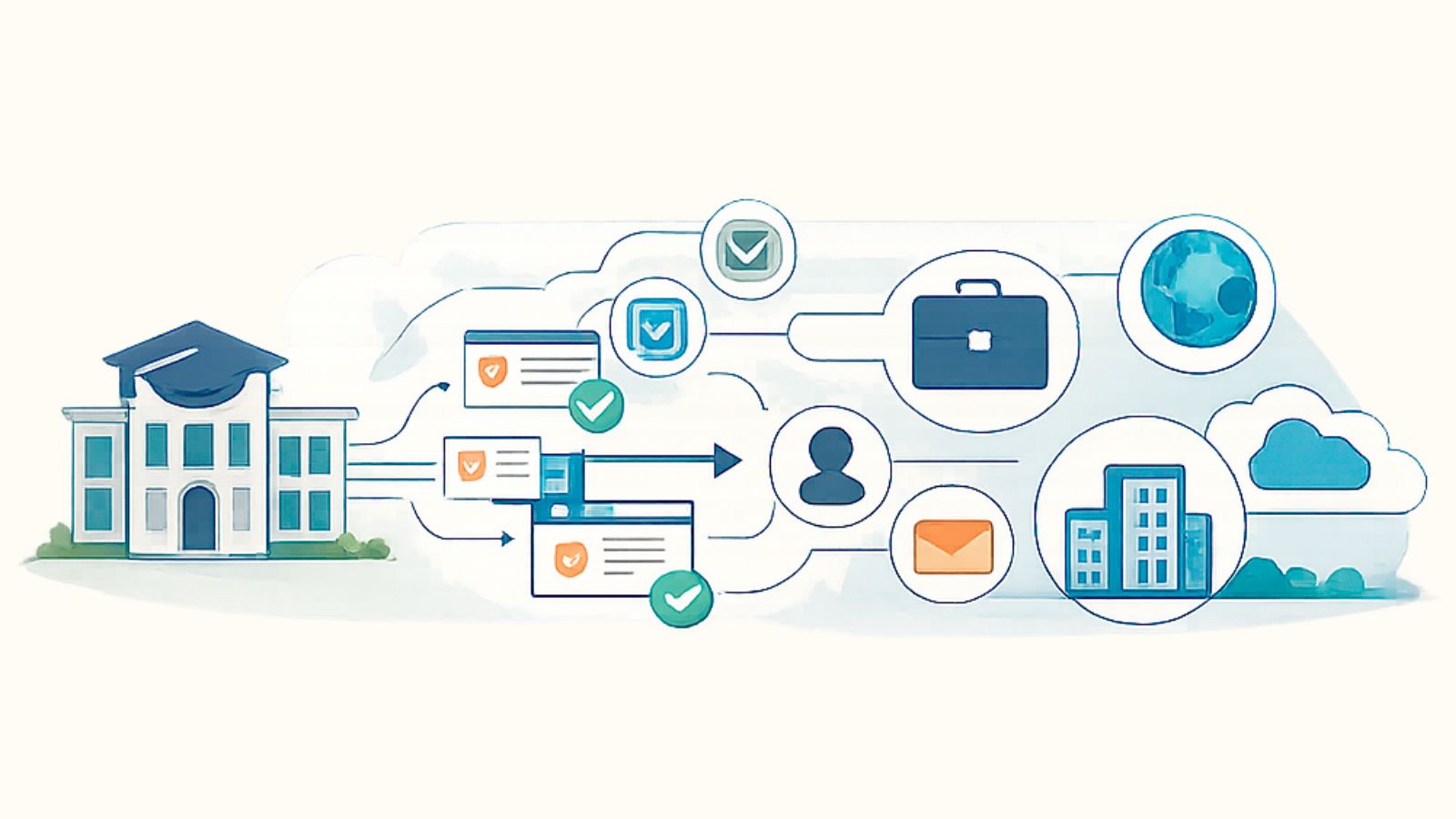 Open Badges standards give learners more autonomy. Credentials can be stored independently, shared flexibly, and retained even if the issuing system changes. On the other hand, platform-dependent credentials may offer a polished experience initially, but can feel fragile outside of the platform itself.
Open Badges standards give learners more autonomy. Credentials can be stored independently, shared flexibly, and retained even if the issuing system changes. On the other hand, platform-dependent credentials may offer a polished experience initially, but can feel fragile outside of the platform itself.
When access breaks years later, learners do not blame standards, but the institutions that issued them.
The Hidden Cost Trade-Offs Institutions Overlook
Cost is usually framed around setup and licensing and that framing hides long-term implications.
Open standards reduce switching costs later. Proprietary credential platforms often optimize for speed and convenience early; but neither approach is universally cheaper. They distribute cost differently across time, especially as credential volume grows.
How institutions should decide on credential standards in practice
The decision becomes clearer when framed around future scenarios.
If credentials are meant to travel widely, be verified independently, and remain accessible long-term, Open Badges standards align better.
If credentials are tightly bound to a specific platform, program, or internal context, proprietary systems may be sufficient.
But the mistake is assuming today’s context will remain stable, indefinitely.
The Five-Year Test for Credential Standards
A simple question clarifies the decision.
If this credential were checked five years from now by someone who has never heard of your institution or platform, would it still verify cleanly?
Open Badges standards are designed to pass this test.
Proprietary systems must be intentionally designed to do so.
For institutions ready to move from principle to implementation, standards often become part of a broader platform decision. Evaluating the top digital credential management platforms through the lens of standards, verification, and long-term portability changes how those comparisons look. The goal is not feature parity, but confidence that the system will still hold up years later.
Final Thoughts
Credential standards are not about ideology. They are about durability.
Open Badges standards prioritize independence, portability, and long-term verification. Proprietary credential systems prioritize control, integration, and immediacy.
The right choice depends on how far your credentials are expected to travel and how long they are expected to matter.
By this point, the real question is no longer whether Open Badges or proprietary systems sound better on paper.
It is whether your credential infrastructure is built to survive change without creating friction later.
If you want to see how standards-based credentials work in a real operational flow, you can schedule a free demo, at your convenience. Chat with our experts to understand how Hyperstack could be your one stop solution for everything digital credentials!
Institutions that treat credential standards as infrastructure rather than formatting decisions are the ones least likely to regret their choice.
Which one are you?
Frequently Asked Questions
Are Open Badges standards required to issue digital credentials?
No, but they significantly improve portability and independent verification.
Can proprietary credentials be converted later?
Sometimes, but conversion is easier when metadata and evidence were designed with openness in mind.
Do employers explicitly prefer open standards?
Employers prefer credentials that verify instantly and consistently, which open standards support more easily.
Are Open Badges standards only for education?
No. They are widely used in education, corporate training, certification, and professional development.
Can institutions support both models?
Yes, when governance is clear and use cases are intentionally separated.
What is the difference between Open Badges and digital certificates?
Open Badges follow a structured, verifiable standard that embeds metadata and verification logic, while many digital certificates are static files that rely on external systems for validation.
Can proprietary credential platforms support Open Badges standards?
Yes. Some platforms issue credentials using Open Badges standards while providing proprietary tooling around issuance and management.
Are Open Badges only relevant for badges, not certificates?
No. Open Badges standards apply to any digital credential, including certificates, micro-credentials, and skill attestations.
Do Open Badges reduce the risk of credential fraud?
Yes, they help by enabling independent verification, issuer authentication, and evidence linkage, making tampering easier to detect.